25% of websites on the internet run on WordPress.
Especially for marketers and developers who want to build their website or e-commerce, WordPress is usually their default option.
However, one of the most common complains people do about WordPress is its security flaws.
Chances are that if you haven’t been attacked is because hackers haven’t paid attention to your site, rather than they can’t.
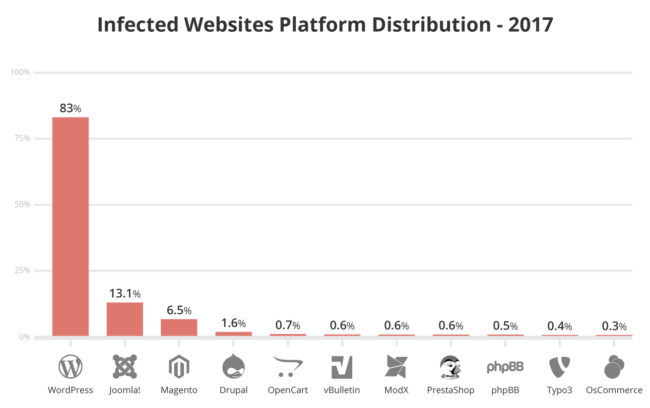
In fact, 70% or WordPress-based sites are at high risk. According to the Hacked Website Report (2017), WordPress was the most infected CMS.
Why WordPress is so insecure?
At its core, WordPress is secure and has a team of experts constantly updating and finding patches. However, as most WordPress users have no technical skills, they’re vulnerable due to bad practices.
Brute force attacks
Brute force attacks are low-hanging fruits for hackers who “guess” WordPress users easy passwords. While it sounds like a joke, many passwords are “password” or “123” which makes it easy for hackers to access and control your site without needing more sophisticated techniques.
This is why WordPress encourages users to use random alpha-numeric passwords.
Outdated versions
The WordPress team does a good job finding vulnerabilities and patching them. Yet, the adoption of these updates is slow, leading to sites to remain vulnerable.
Vulnerable WordPress plugins and themes
Besides running sites on outdated versions, another fundamental reason is the nature of WordPress being open-source; anyone can build plug-ins, templates, themes, and add-ons with no scrutiny or control.
Most of WordPress users are not avid technically or don’t code. That’s why they (including me) rely on plugins—plug-and-play solutions for any aspect of a site.
While most of the WordPress community follows the development standards, there is no quality check besides forums, comments, and reviews, so it may happen that users don’t update to the latest plugins versions or worse, the developers stop to provide support, and updates.
Some of the massive attacks, compromising hundreds of thousands of websites are due to popular plugins facing such vulnerabilities. Some popular plugins that have been vulnered are:
WooCommerce: being the WordPress official plugin to let you convert your WordPress site to e-commerce, it has been installed in over 5 million sites. Since 2014, WooCommerce has reported 19 vulnerabilities. One of them allowed users with Shop Manager role “scale privileges” to take full control of websites.
E-commerce vulnerabilities are especially sensitive as these sites potentially store personal and financial data.
SEO Yoast: I’m a Yoast user – it’s my default plugin to handle basic technical SEO tasks. However, I’ve been constantly tempted to switch to alternatives like RankMath as complaints on forums and Facebook groups started to be common.
One of the most renowned Yoast vulnerabilities was called a Race Condition, which allowed attackers t o run undesired actions on your website. Again, the vulnerability was quickly fixed but most users still have outdated versions of the plugin.
Ninja Forms: this form plugin is installed in over a million sites and it faced a high-risk vulnerability that could enable attackers to take admin permissions and, basically, steal your website.
Fortunately, these plugins have a large community and great support; most of the patches were made within hours.
Common WordPress vulnerabilities
These are some of the most common vulnerabilities WordPress is exposed to, mainly due to poor passwords and insecure plugins.
Arbitrary file upload
Every website needs forms to collect users’ data and most WordPress users rely on form plugins to set them up.
Ocasionally, some form plugins have been found to be vulnerable to arbitrary file uploads.
Those who develop these plugins need to make sure certain conditions are met to let users fill or execute such forms. For instance, restricting permissions to a specific kinds of users or just a type of content can be submitted (e.g. images).
Otherwise, attackers may upload any kind of files like malicious scripts that may compromise sensitive website’s data found on servers or databases.
One example of a famous plugin with an arbitrary file upload vulnerability was WooCommerce Checkout manager.
SQL injections
While they sound cool, SQL injections can lead a website to compromise sensitive information, be blacklisted on Google, and hosting suspensions.
Like arbitrary file uploads, hackers may find vulnerabilities in places of your site where they can add inputs or data, like search bars or forms to run scripts that your database won’t verify.
Privilege escalation
These vulnerabilities may lead to a user with a subscriber role scale to admin permissions, which would give them full control of your website.
VirusDie: a Wordfence alternative
While Wordfence is one of the standard solutions for WordPress users, VirusDie outperforms it in many aspects. For instance, it goes beyond WordPress.
Holistic malware detection: VirusDie world-best detector features an incredibly extensive database to detect as many viruses and threats as possible, including brand-new threats. Antivirus database updates automatically in the background in real-time.
Wordfence falls short to catch some types of malware that other scanners can, making necessary to double-check with other security tools.
False positives: False positives occur when you get notifications of threats when they’re not happening, causing eventual confusions or mistrust.
VirusDie offers the lowest false positive 0.0002%; that’s an error every 500,000 alerts.
Malware cleanup: VirusDie doesn’t only delete malicious files, it can also spot fragments of malicious code within other files, ensuring website uptime.
Plugins vulnerabilities detection: Unlike Wordfence, which only works on WordPress, VirusDie performs security audits on all CMS.
Blacklist monitoring: Being blacklisted may hurt email deliverability and prevent search engines to even list your site. VirusDie monitors dozens of hosting providers to check if your site is being blacklisted.
Malicious code highlighting: Seamlessly visualize malicious fragments of code in your files to analyze and delete them. You can also get full virus descriptions and recommendations on such attacks.
PDF reports: you may get automatic reports to track the security performance of your website that you can share with your team or any stakeholder.
Want to try VirusDie today?
VirusDie is the friendliest antivirus to secure all your websites. Pitch Ground has yearly deal at a fraction of the regular price for a limited time.